Fully Homomorphic Encryption: the business applications
Fully Homomorphic Encryption creates many new ways we can use our encrypted data. What applications are already out there, and what may be possible in the future?
There are not many organizations that already use FHE. Who does (and how), and what is possible?
Estimated reading time: minutes
This post is part 4 of the Fully Homomorphic Encryption series.
Current applications Permalink
Because Fully Homomorphic Encryption is still in a fairly experimental phase, few organizations are using the technology yet. The companies that already use FHE are, for example, IBM, Microsoft and Google.
IBM field trials Permalink
IBM says it has implemented FHE in two cases. Once in 2019 at the Brazilian bank Banco Bradesco 1 and a second time at a European bank 2 (the research paper of which has not yet been published). At Banco Bradesco, there was a need for a machine learning model that could work securely with financial data from their customers. This data had to be used to predict whether a specific customer would apply for a loan in the next three months. FHE can help with this issue as it allows the bank to safeguard the privacy of their customers while gaining useful insights about the customer’s condition. The customer can then receive a better offer or be helped out in another way.
To achieve this, all financial data and the machine learning model itself are first homomorphically encrypted 3. Subsequently, IBM was able to demonstrate that it was possible to perform predictions with the same accuracy as without encryption. Finally, the model was also trained with encrypted data, which showed that it is possible to use FHE to guarantee privacy in this case. This means that it seems quite possible for banks to really start using this technology. This allows them to safely outsource prediction execution to an untrusted environment.
Password monitoring Edge and Chrome Permalink
The most used application of FHE at the moment, is probably the password monitoring function of Microsoft Edge 4 and Google Chrome 5. The web browsers offer the functionality of a password vault, so it is important to properly protect information within this function. To encrypt passwords, while retaining the ability to compare them to a database of leaked passwords, homomorphic encryption is used. Microsoft uses a modified version of their SEAL FHE solution in Edge. All passwords (and usernames) are hashed and made unreadable with a traditional form of encryption (see Figure 1) 4. The information is then homomorphically encrypted. The highly encrypted information is sent to the cloud to be compared against huge password databases. The results of this are processed locally by the user to determine whether the checked username and password combination actually exists in the database. If this is the case, the user will see a warning (see Figure 2) 6. The implementation in Google Chrome works in a similar way.
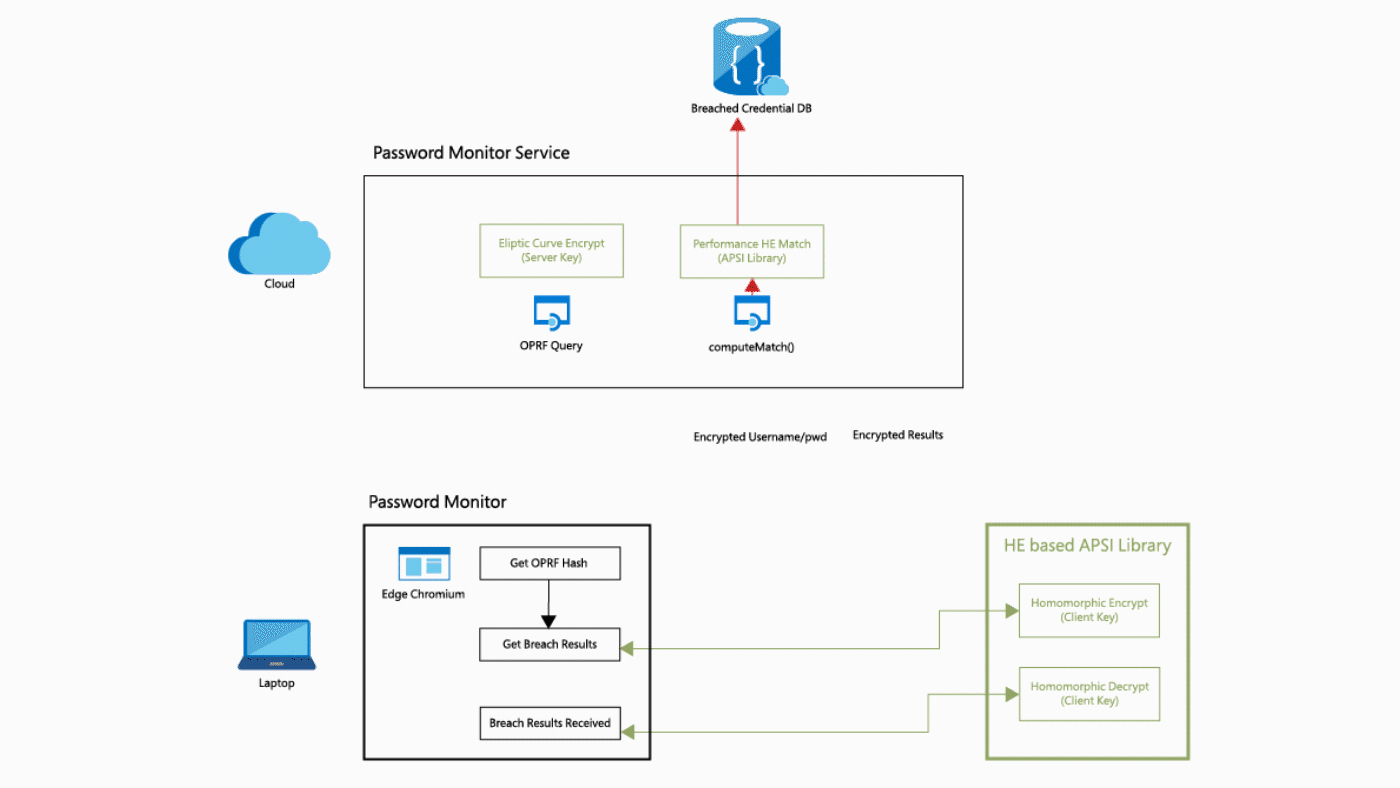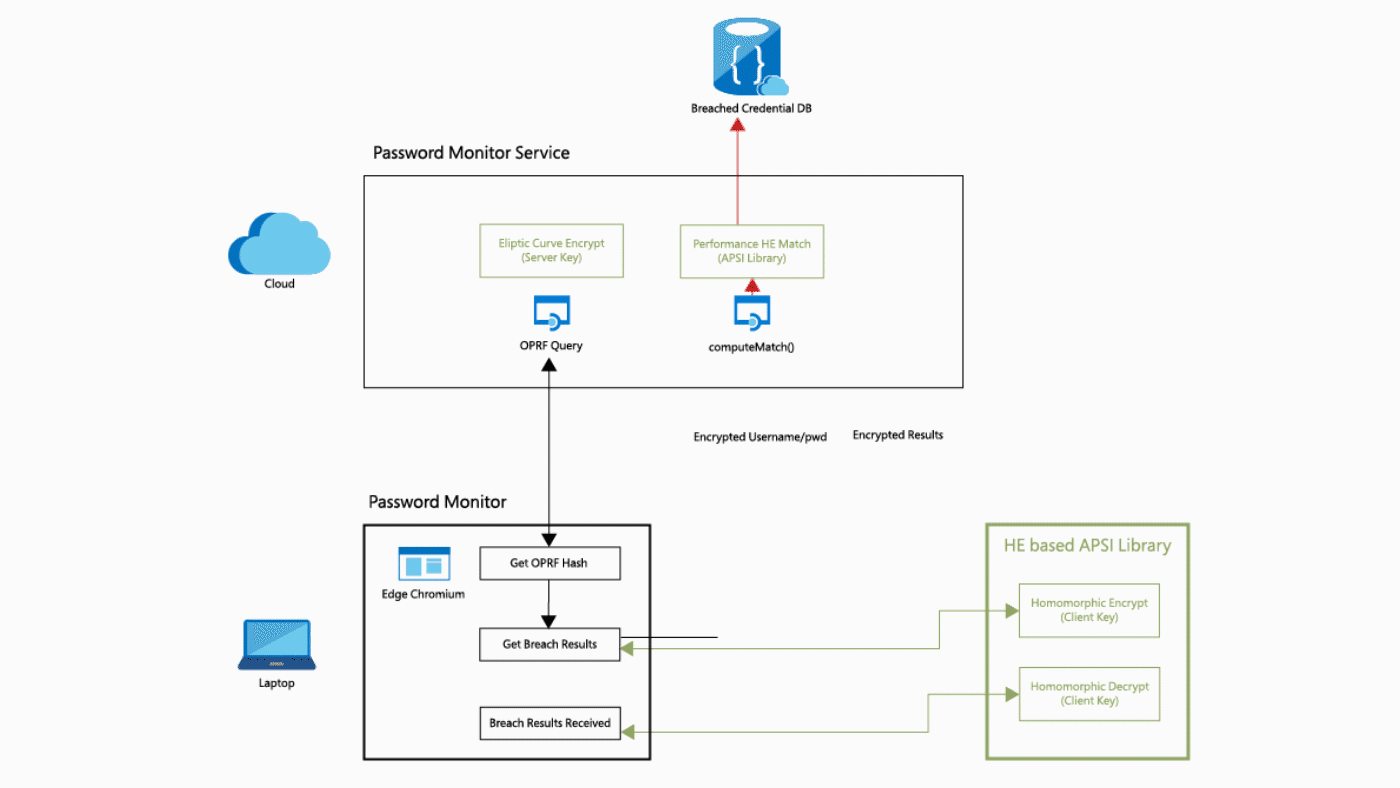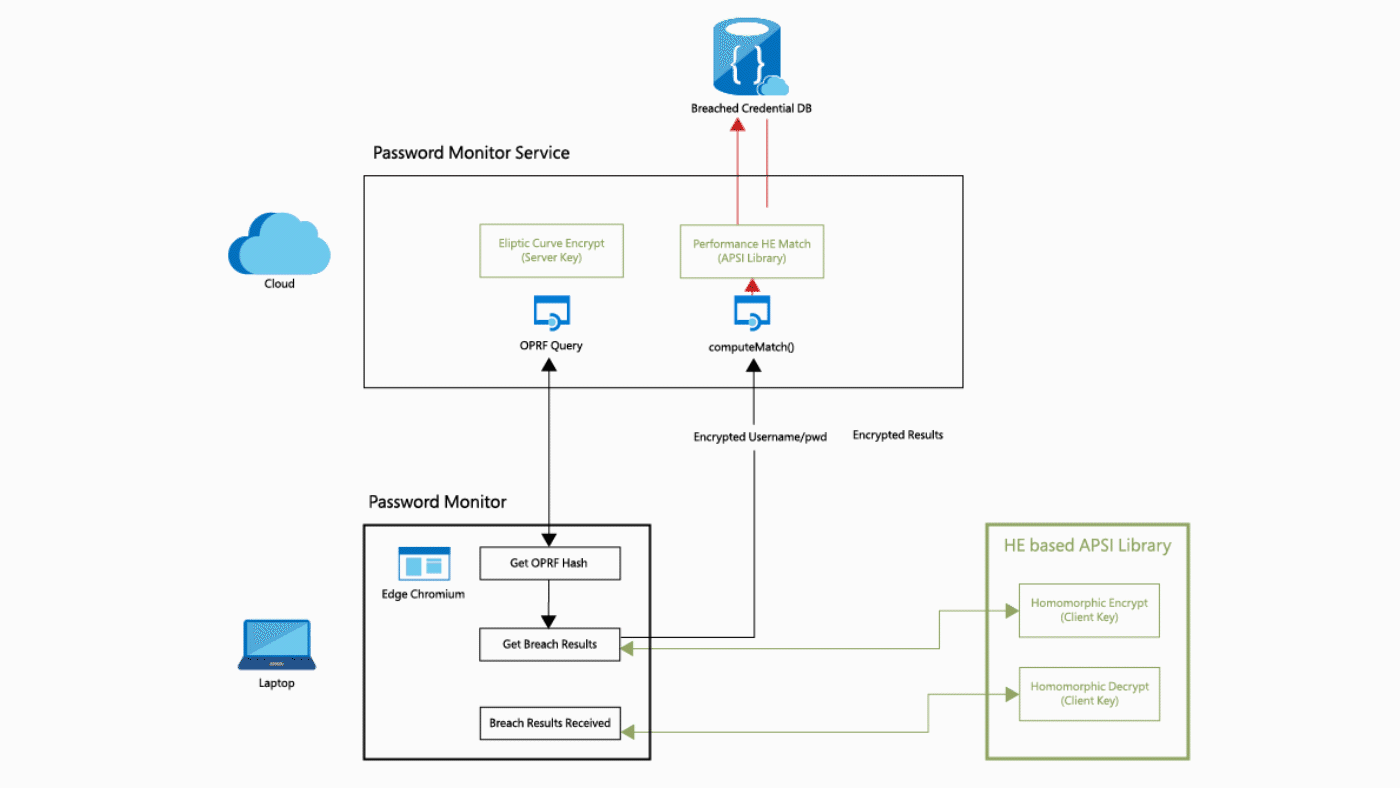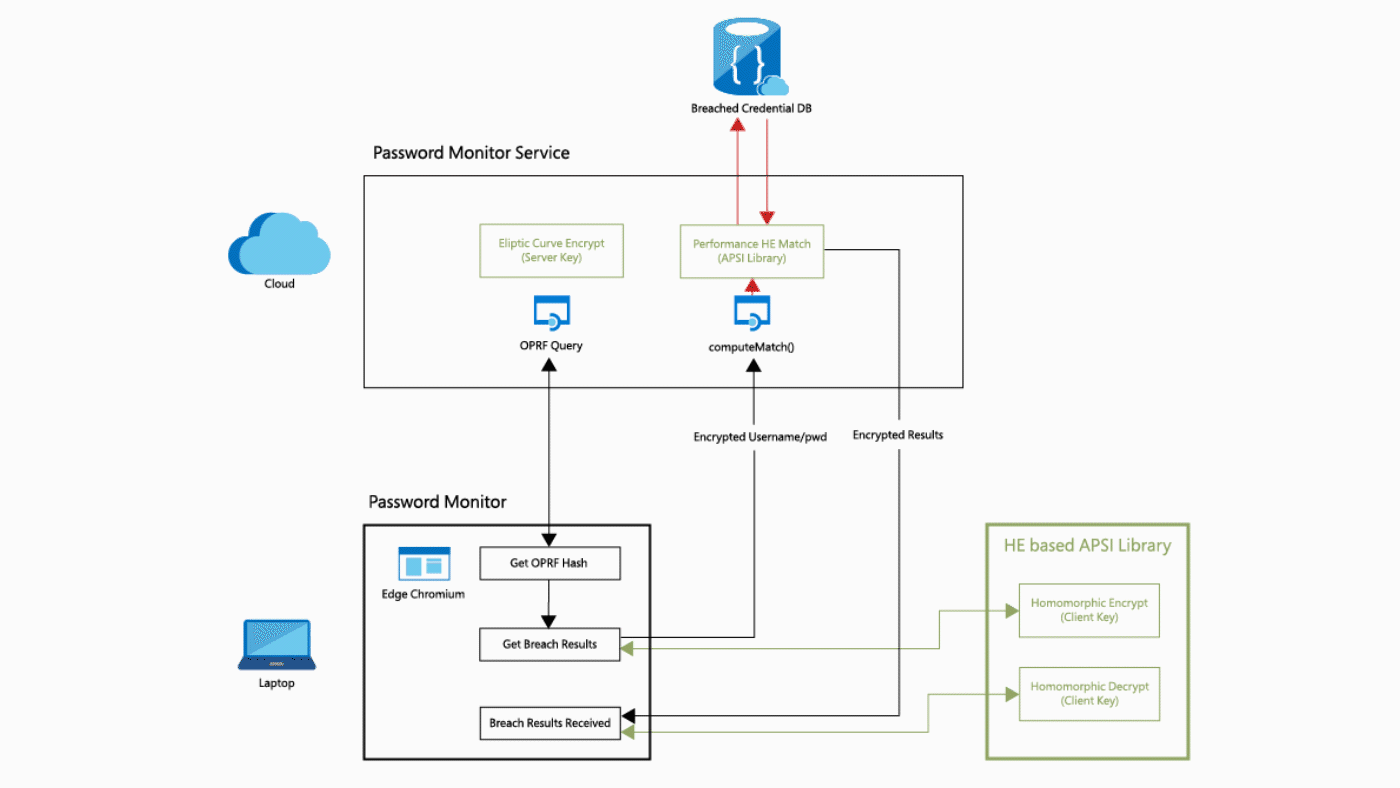
Figure 1. Edge Password Monitor HE flow diagram.
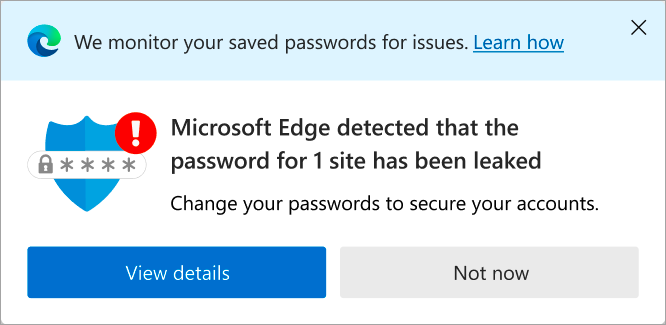
Figure 2. Edge Password Monitor popup.
Microsoft ElectionGuard Permalink
A final example of FHE in practice is Microsoft’s product ElectionGuard 7. It provides a way to verify that election results are correct, and that votes have not been altered, suppressed, or otherwise been tampered with in any way. Individual voters can see that their vote has been registered and that their choice has been correctly added to the final count. Anyone who wants to follow the election can verify that all votes have been tallied correctly to obtain an accurate and fair result. The principle of secret ballots means not only that each person’s vote should be private, but must be private so that votes cannot be bought, sold or coerced.
ElectionGuard uses FHE to ensure this. Each voter receives a tracking code to verify that their vote goes through the system unchanged and ends up in the final count. However, this code cannot be used to prove how a vote was cast, it can only be proven that the vote has not been changed. During the count, all encrypted votes can simply be added together, without anyone ever being able to see the content of the vote.
Possible applications Permalink
So FHE is already being applied in a number of ways in practice, but what other applications are possible?
Icons made by Good Ware, photo3idea_studio, srip, Freepik, dDara and Eucalyp from www.flaticon.com
This article is based on a research report I wrote for the project “Fully Homomorphic Encryption” commissioned by [SALT Cyber Security]. You can also read this blog post (in Dutch) on their website at https://salt-security.com/nieuws/fully-homomorphic-encryption-de-geschiedenis/.
O. Masters, et al., “Towards a Homomorphic Machine Learning Big Data Pipeline for the Financial Services Sector”, 2019. [Online]. Available: https://eprint.iacr.org/2019/1113.pdf. ↩︎
J. Salter, “IBM completes successful field trials on Fully Homomorphic Encryption”, Ars Technica, Jul. 31, 2020. https://arstechnica.com/gadgets/2020/07/ibm-completes-successful-field-trials-on-fully-homomorphic-encryption/. ↩︎
K. Moskovitch, “Top Brazilian Bank Pilots Privacy Encryption Quantum Computers Can’t Break | by Inside IBM Research | Medium”, Inside IBM Research, Jan. 10, 2020. https://ibm-research.medium.com/top-brazilian-bank-pilots-privacy-encryption-quantum-computers-cant-break-92ed2695bf14. ↩︎
K. Lauter, S. Kannepali, K. Laine, and R. C. Moreno, “Password Monitor: Safeguarding passwords in Microsoft Edge”, Microsoft Research, Jan. 21, 2021. https://www.microsoft.com/en-us/research/blog/password-monitor-safeguarding-passwords-in-microsoft-edge/. ↩︎ ↩︎2
J. Pullman, K. Thomas, E. Bursztein, “Google Online Security Blog: Protect your accounts from data breaches with Password Checkup”, Google Security Blog, Feb. 6, 2019. ↩︎
Microsoft, “Protect your online accounts using Password Monitor”, Microsoft Support. https://www.microsoft.com/en-us/research/blog/password-monitor-safeguarding-passwords-in-microsoft-edge/. ↩︎
A. Thornton, “What is ElectionGuard?”, Microsoft On the Issues, Mar. 27, 2020. https://news.microsoft.com/on-the-issues/2020/03/27/what-is-electionguard/. ↩︎
